
From CryptoNets to Calum McClelland’s in-depth series on “Securing the Internet of Things,” security has been a hot topic that we’ve covered here at IoT for All. If the Dyn DDoS attack has taught us anything, it’s that our IoT infrastructure is outpacing the development of adequate security measures, and this is just as true for the smart city.
To that point, here we analyze an excellent report by Kaspersky Lab that flew under our radar last September, which exposed several weak points in our smart city technology stack — including hilarious hacks of electronic road signs.
Hacking Touchscreen Kiosks
Whether you’re at an airport, a parking lot, or a movie theater, you’re now more likely to use a touchscreen kiosk to skip the line. These kiosks are simply PCs with a touch screen operating in ‘kiosk’ mode, an interactive graphical shell with limited functionality.
Users shouldn’t be able to exit the kiosk mode and get access to the main OS, let alone easily. But in reality, the process to exit the kiosk mode is as simple as right-clicking to exit full-screen or clicking on external links.
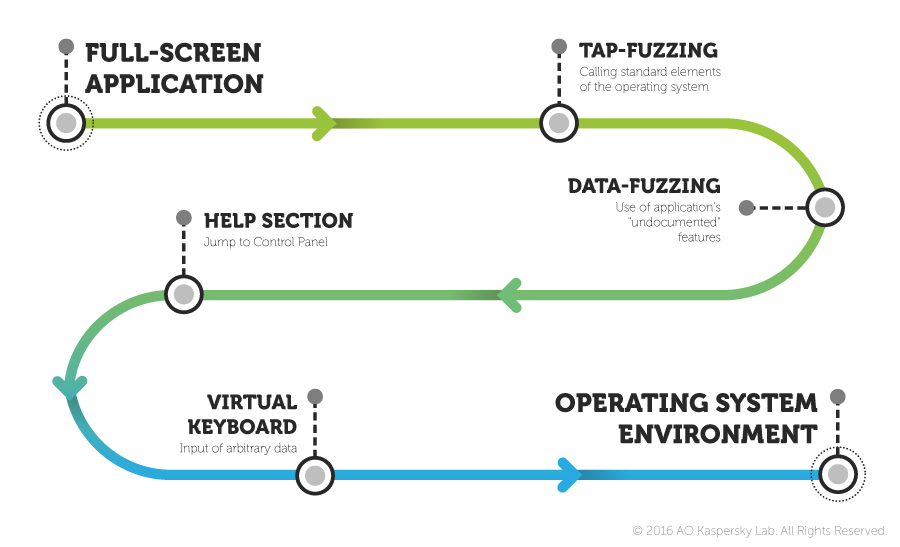
Techniques to Get Access to the OS Environment:
1. Tap Fuzzing: A hacker looks for a vulnerability or incorrect handling of touch interactions such as dragging fingers on the screen corners or long-pressing on certain elements on the screen. This will bring up OS access to object properties or I/O system, enabling the hacker to explore the PC’s hard drive.
2. Data Fuzzing: A hacker might also enter incorrect data into the entry fields to trigger an unhandled exception. The OS will try to handle the exception by notifying the user, and the hacker can access the control panel via the help section afterward.
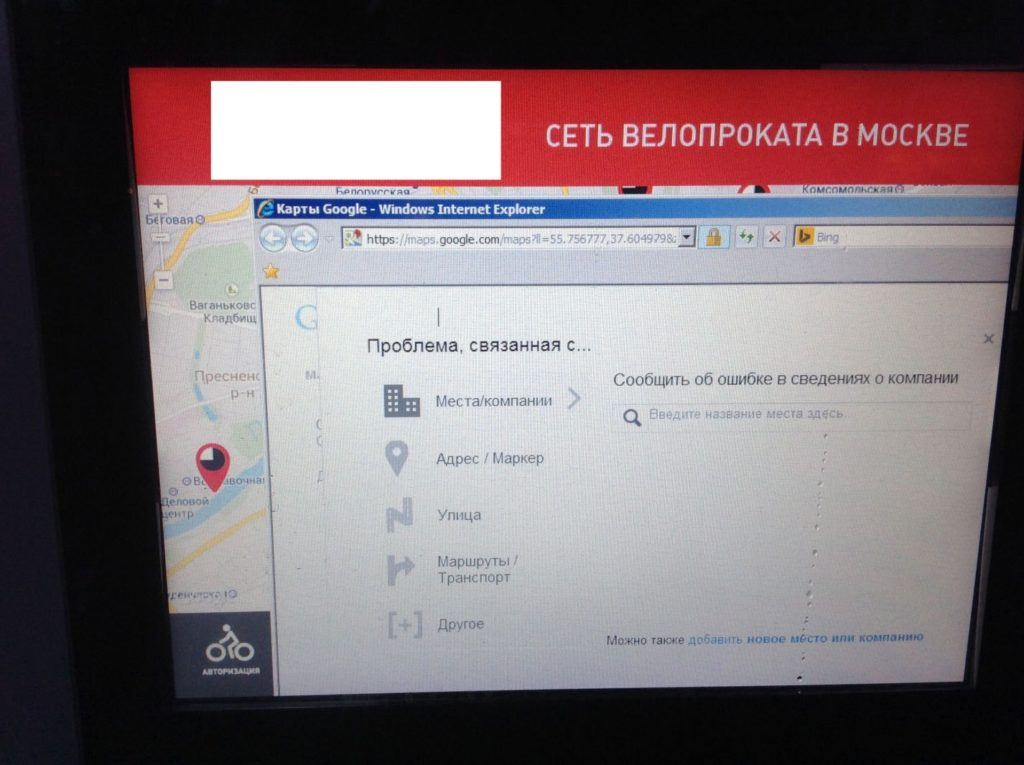
3. External Links: Sometimes the hacker is able to click on external links on the Kiosk such as Google Maps or Facebook to exit the kiosk mode and bring up a standard browser environment.
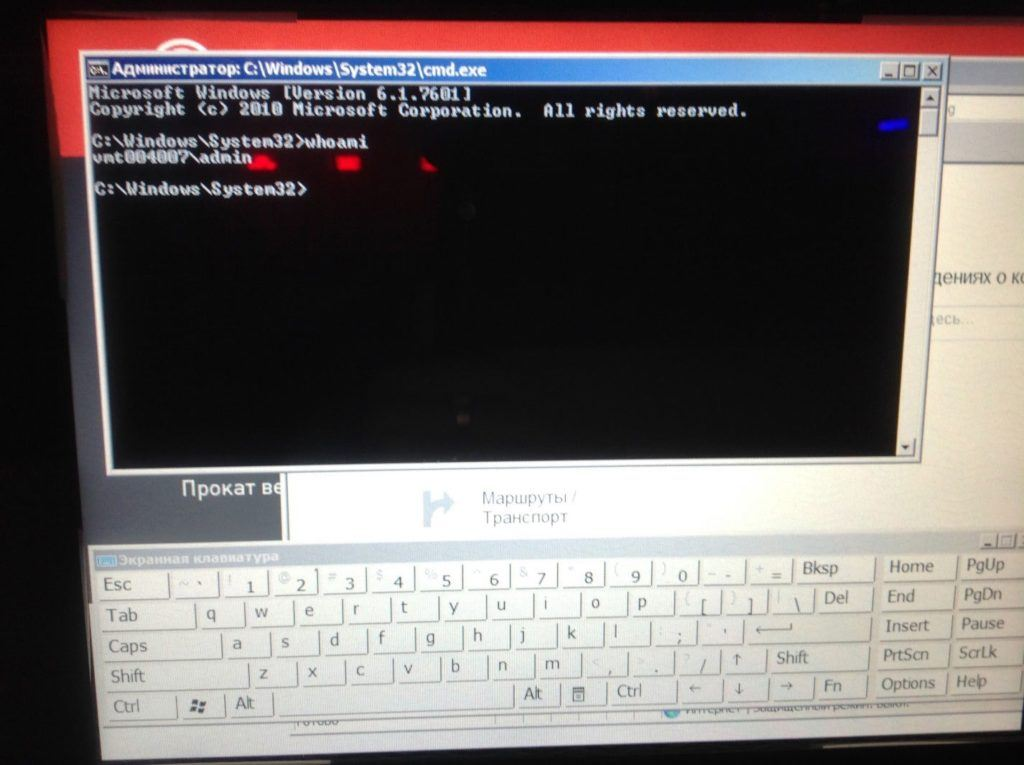
The Kaspersky Team was able to click on the “Report an Error” and “Privacy Policy” button on Google maps widget to exit out of the kiosk mode. After the team pulled up the web page, they opened up cmd.exe by using the virtual keyboard and found that the application was running with admin privileges, meaning that the user has access to nearly everything on the kiosk.
This is troubling since the hacker can easily extract collected information on the kiosk such as names, emails, phone numbers, and possibly payment options. Even if the hacker cannot retrieve your credit card information, the personal information alone could be worth a hefty sum to data brokers (as explored in our story “You’re Being Sold on the Internet”).
The authors of the report also demonstrated how easy it was to hack into kiosks at government offices by long pressing the Change Printer button; clicking on ads on airport kiosks then subsequently opening an additional browser window, and getting root access to Android OS on taxi payment panels.
Smart City Recommendations
To protect against malicious attacks by hackers on kiosks, the Kaspersky Team recommends the following steps:
1. Disable extra functions that invoke OS menus such as right mouse click, links to external sites, etc.
2. Store valuable information on the server rather than the device itself.
3. Launch the kiosk mode using sandboxing technology to limit functionality.
4. Deny administrative access to the kiosk’s OS.
5. Deploy each device with unique passwords to prevent hackers from easily accessing other kiosks if one of them is compromised.
We might be several years away from a vast network of sensors deployed in “smart cities.” But considering the ubiquity of kiosks right now in our public domains, we should consider patching up our security in existing connected devices before we talk about securing our up-and-coming IoT devices.






 Latest IoT News
Latest IoT News









