How to Secure IoT Smart Meters
How to Secure IoT Smart Meters
- Last Updated: December 2, 2024
Guest Writer
- Last Updated: December 2, 2024



Governments and utilities continue to leverage IoT device manufacturers to support massive IoT deployments to digitize and modernize legacy energy systems. These parties recognize that smart metering is fundamental to citywide smart grid systems and the shift toward sustainability. In the US alone, two major electricity providers, PSE&G and Atlantic City Electric, plan to install 2.3 million smart meters by 2024. However, today’s rapidly evolving smart meters security landscape poses several challenges to utilities and their IoT partners.
"Governments and utilities continue to leverage IoT device manufacturers to support massive IoT deployments to digitize and modernize legacy energy systems."
Important Considerations for Smart Metering Solutions
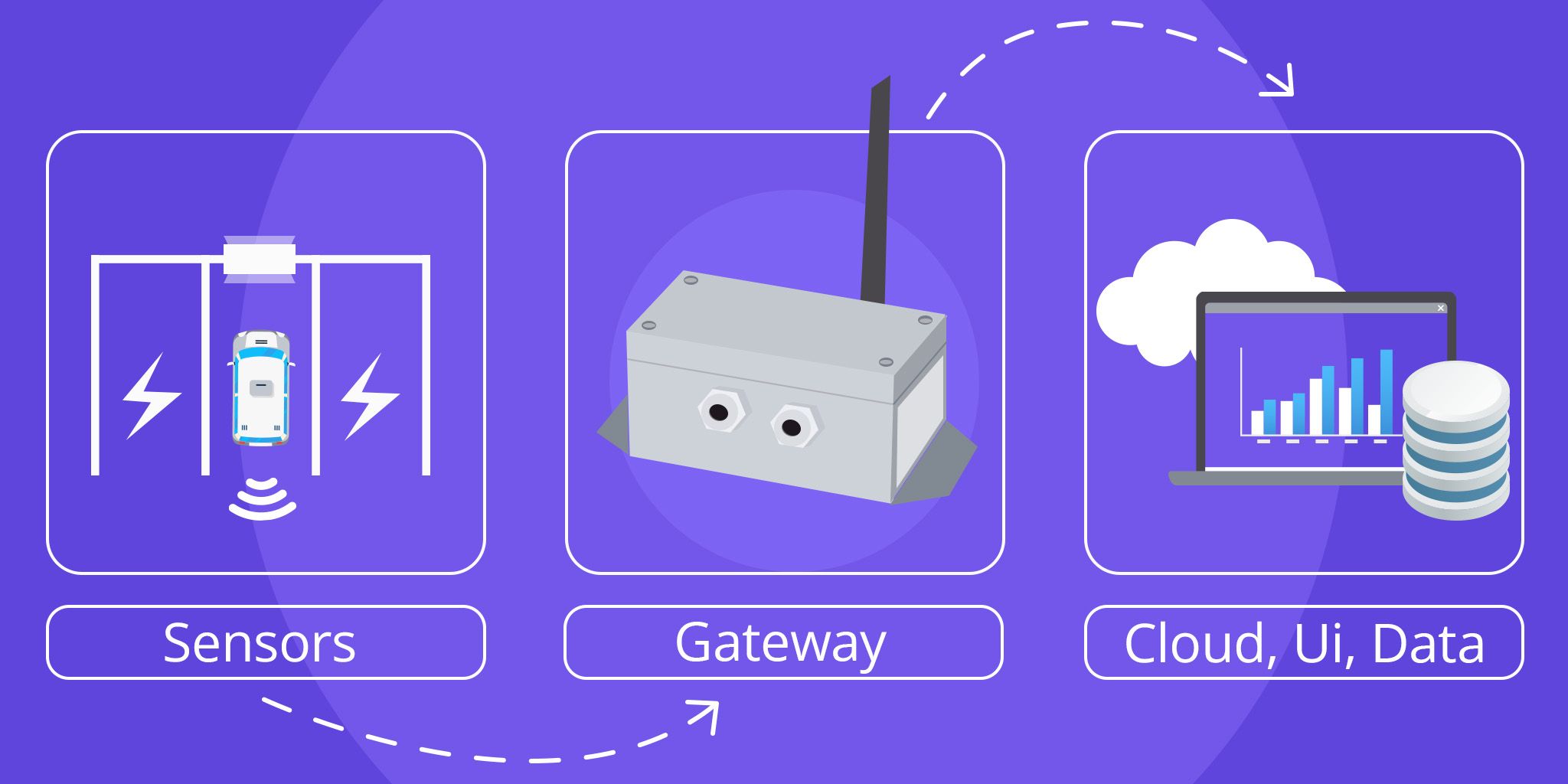
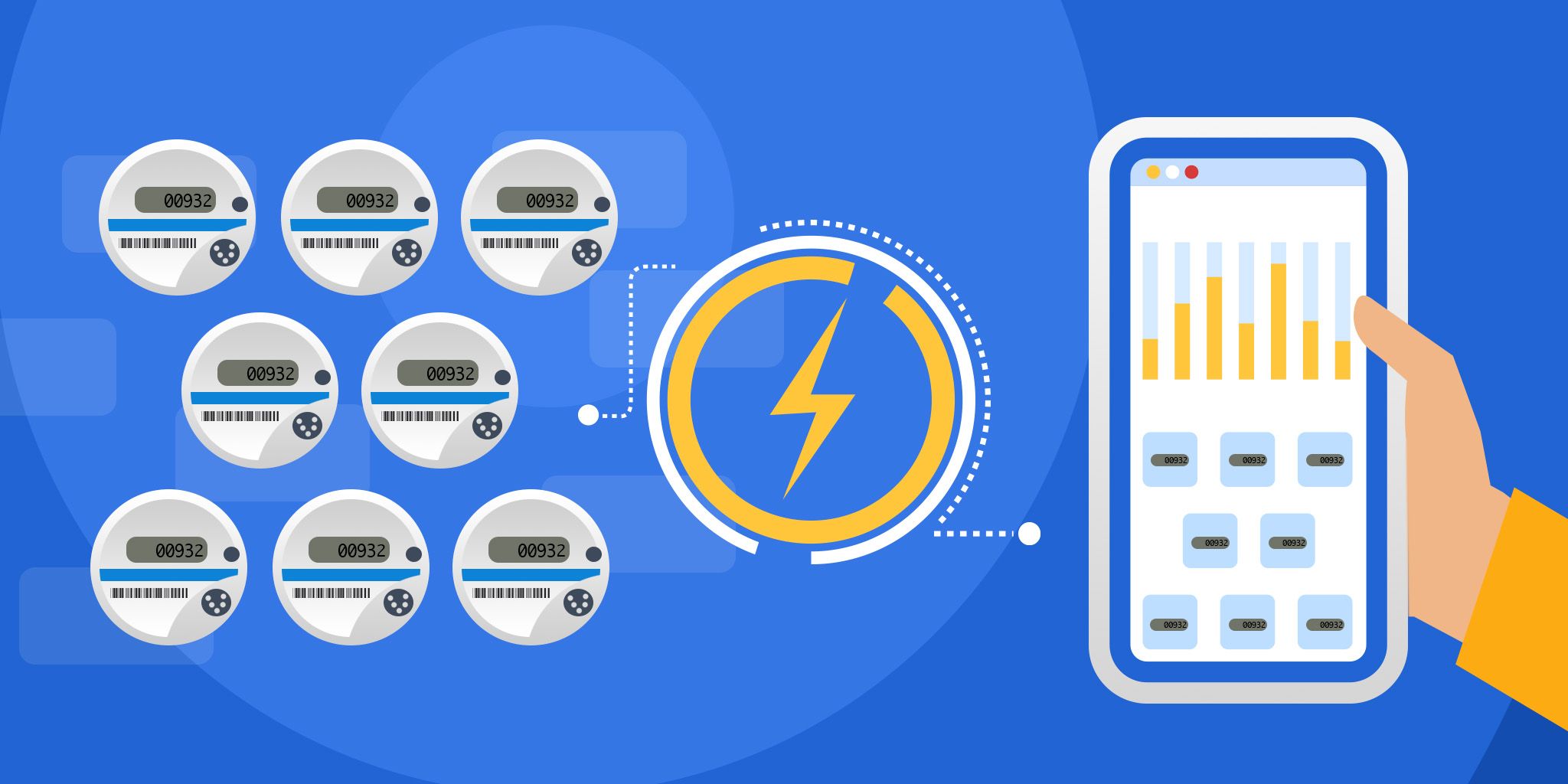
Smart metering systems leverage Internet of Things (IoT) devices and sensors to collect, analyze, and send data through alerts and diagnostics to different utility companies in the water, oil, gas, and electricity verticals. This data collected through smart metering systems help utilities optimize distribution, decrease operational costs and enable customers to make more informed usage decisions.
Likewise, smart metering allows utilities to balance electric loads, forecast usage accurately, and boost customer trust via reliable billing. Moreover, it supports remote monitoring and automatic routing, eliminating the need for truck rolls and sending technicians on-site to resolve power outages.
Despite the numerous benefits of smart meters, there are key considerations every IoT device manufacturer must address when deploying these solutions for their utility customers, including connectivity and design factors, and – most importantly – security.
Who Controls IoT Firmware?
Because IoT devices contain modules, which run on firmware, it is paramount that IoT device manufacturers have a trusted module supplier for smart meters security. Firmware is software embedded into a device that allows it to run effectively and communicate with other software; likewise, firmware is foundational to a device’s operating system and security.
However, IoT device manufacturers often have little to no knowledge of the details surrounding the code running inside their modules. The module manufacturer, or author of the code, is the only party that fully understands the functionality of the module. The module manufacturer chooses what the IoT device manufacturer can see through the attention (AT) interface, highlighting the necessitate of a trustworthy supplier.
Also, the IoT device manufacturer must rely on the module manufacturer to ensure that the module can adapt to firmware updates for maintenance, network changes, or security updates. With an IoT module approach, device manufacturers simply don’t have visibility into who wrote or signed off on a large portion of the firmware running inside their devices.
Connectivity and Security
In addition to having a trustworthy module supplier, IoT device manufacturers will need to choose a connectivity standard to keep their utility customers’ smart metering solutions operational. There are a variety of options for connectivity, with cellular LPWA, specifically LTE-M and NB-IoT, being the most common. Security goes hand-in-hand with connectivity, as any time a device connects to the Internet, it opens up the possibility of exploitation by bad actors. IoT device manufacturers must consider these vulnerabilities when protecting their device's network connections.
Careful Module Supplier Consideration
Partnering with an unscrupulous or inept module supplier is not without consequences. Last year, the Czech government warned of potential cybersecurity threats, having identified these high risks through software like smart meters, emphasizing the questionable trustworthiness of a supplier’s business operations.
Should an IoT security breach occur, the results can be severe. Data could get corrupted, causing errors; likewise, security breaches can cause mass disconnections of thousands of consumption points, leading to blackouts, which will cause significant society-wide disruptions. To make matters worse, cyberattacks against IoT devices, like smart metering solutions, are on the rise.
Selecting an Optimal Vendor
IoT device manufacturers must perform due diligence and vet module suppliers accordingly. First, verify if the vendor has references for government-supported and critical infrastructure projects. Also, IoT device manufacturers should ask a potential supplier to demonstrate robust quality procedures aligned with regulations.
If doubts arise concerning the legal or political environment in which the supplier operates, it's best to err on the side of caution. Additionally, to ensure smart metering solutions are as secure and effective as possible for utility customers, it is helpful to seek the guidance of a trusted IoT advisor with experience deploying large-scale projects and smart meters security.
The Most Comprehensive IoT Newsletter for Enterprises
Showcasing the highest-quality content, resources, news, and insights from the world of the Internet of Things. Subscribe to remain informed and up-to-date.
New Podcast Episode

Navigating the Future of Embedded Computing
Related Articles