AI Biometric Authentication for Enterprise Security
AI Biometric Authentication for Enterprise Security
- Last Updated: December 2, 2024
MobiDev
- Last Updated: December 2, 2024



Biometric authentication technology has been an important industry trend for years, especially in 2021 due to the latest AI innovations available on the market. According to IBM, 20 percent of breaches are caused by compromised credentials. Worse, it can take an average of 287 days to identify and respond to a data breach.
AI-based security is increasing in usage and will be necessary to remain competitive in any industry. IBM reports that as of 2021, 25 percent of businesses have completed deployment of AI-based security, while another 40 percent are partially deployed. The remaining 35 percent have not yet begun this process, and if your business falls into this third category, you may be placing your clients at great risk for dangerous data breaches. Investing in AI-based security is projected to help save a business up to $3.81 million in 2021.
Being able to use artificial intelligence to identify and automatically respond to data breaches is incredibly important for protecting the data and privacy of a company and its customers. AI biometrics authentication provides yet another safeguard against a data breach, making it essential for businesses of any scale. Not only that, but IBM’s study shows that correct use of AI security platforms will cost businesses less in the long run. It is extremely important to understand and consult with experts in the security field to develop a solution optimized for your business.
AI-powered biometrics analysis and authentication are used to secure a system from malicious actors using not just a password, but who you are: your fingerprints, vocal data, and iris scans.
With more advanced biometric authentication, verification, and identification technology at our disposal in 2021 than ever before, we can make industry systems more secure while maintaining efficiency and accessibility. Let’s talk about how biometric authentication works, and the most important new trends such as artificial intelligence biometrics.
Biometrics Technology Overview
At first glance, biometrics may appear to simply be a way of accessing a cell phone more quickly while retaining security, but there are many more benefits than this convenience. At its core, the objective of biometric security technology is to improve security by using parts of our bodies that cannot be easily replicated. Although machine learning and quantum computing may be able to guess a password, biometric information like fingerprints, faces, and irises are not so easily determined or emulated.
According to Statista, the biometric technology market will be valued at $55.42 billion before 2027.
Over the range of 10 years from 2017 to 2027, worldwide spending in the identity verification market is anticipated to grow by more than 13 billion U.S. dollars, increasing from $4.93 billion in 2017 to over $18 billion in 2027. Identity verification is an important aspect of information security, as it ensures that only the people with legitimate authority to access information are able to do so, thereby preventing harmful or malicious intrusion to protected information.
Types of Biometrics
Biometrics technology can be split into three domains: identification, verification, and authentication. Identification is used when the system wants to know who the user is. Verification is about using that biometric information to determine whether it aligns with the other information associated with the user. Finally, the goal of authentication is to understand if the identity the user claims to be is correct and authorized to access the services and data they are requesting.
As an example, biometric identification may be used to determine the identity of a user against a database of faces. Law enforcement facial recognition databases use this technology to great effect and can help investigate security camera evidence footage with better accuracy than a human. Verification is helpful for ensuring that the user and the information stored in the database about them match. Authentication is perhaps the most critical of the three, enabling authorized users to access sensitive information while restricting unauthorized persons.
The table below shows the various characteristics of each type of biometric technology.
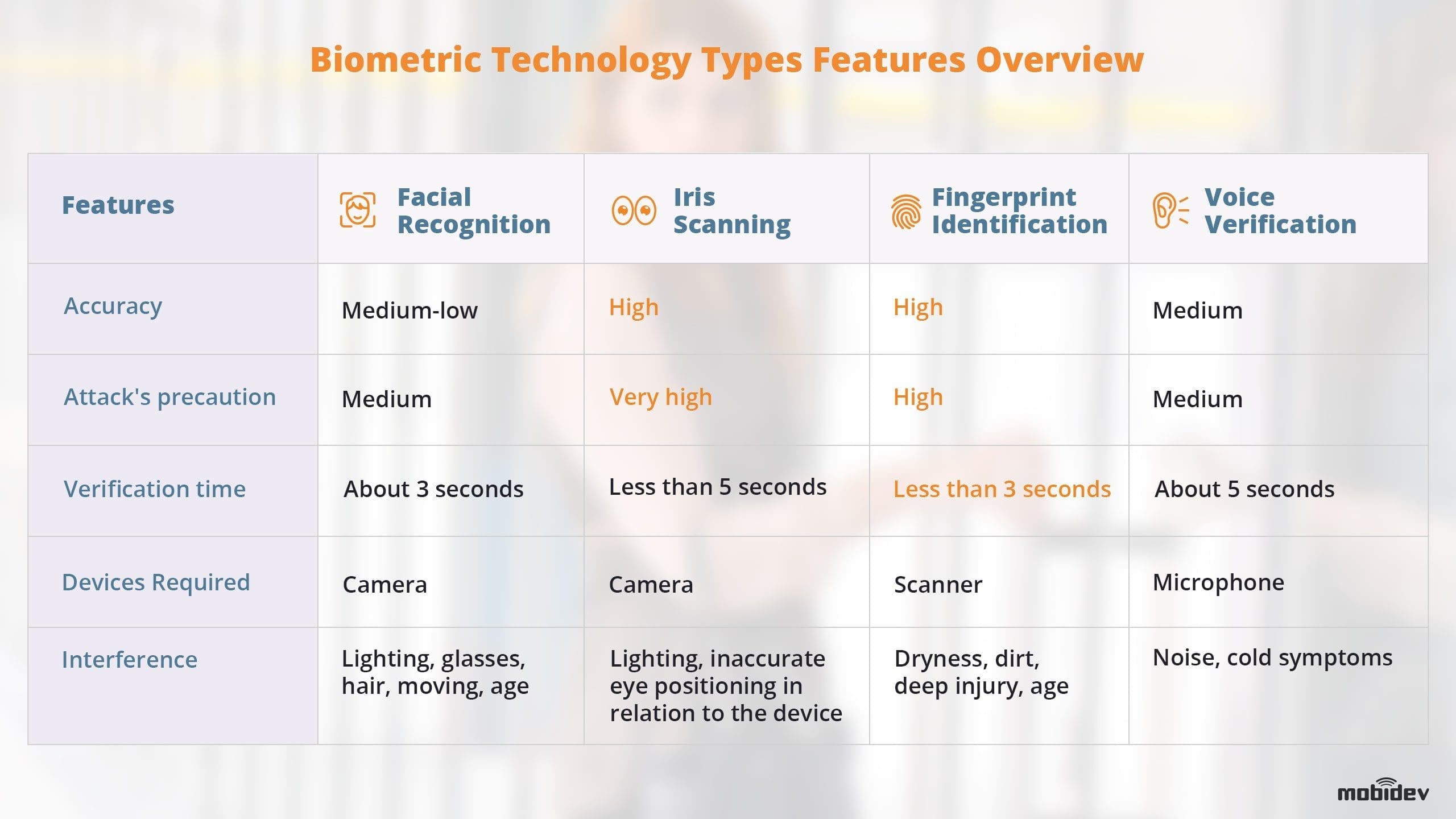
Source: MobiDev
One of the most important takeaways for any business considering biometric security methods is that it is not always wise to depend on only one form of biometric technology, i.e. unimodal. Instead, a multimodal approach that uses more than one type of biometrics is much more secure.
Facial Recognition Technology
The facial recognition market was estimated at $3.8 billion in 2020. This market is projected to grow in the coming years, reaching $8.5 billion by 2025.
Biometric authentication technology that uses facial recognition has been a valued feature for security for years, making its way onto millions of iPhone and Android smartphones. With advances in augmented reality and machine learning focused on aiding computer recognition of human faces, facial recognition technology has become more sophisticated than ever before in 2021.
One of the reasons why facial recognition technology has improved for identification and authorization this year is because of the necessities brought on by the pandemic. Due to the increased usage of face coverings like masks, facial recognition has become more difficult with fewer data points from which to match a person's identity. However, many facial recognition solutions can now account for hurdles like face coverings. This is not only good for consumer convenience but also helpful for law enforcement officers attempting to identify criminals. By matching the face of the subject with a database, subjects can be identified even if they are wearing a mask.
Since 3D cameras can get much more information about a human face than a two-dimensional camera would, facial recognition is also much more secure now as a biometric authentication technology. Previously, it was much easier for computers to be fooled by a photograph of someone’s face or even just a similar-looking face. However, machine learning has helped narrow the margin of error to prevent hackers from exploiting facial recognition-based security, and various anti-spoofing methods now exist.
Voice Recognition Technology
The global voice recognition market size was forecasted to grow from $10.7 billion in 2020 to $27.16 billion by 2026.
Hands-free communication has been enriched greatly by voice recognition biometrics technology for language processing purposes. However, voice recognition has another purpose: identification. Smart home device ecosystems like Google Home, when trained, can identify different members of a household by using voice recognition to differentiate between them. This is helpful for displaying information pertinent to that individual, such as their calendar and notifications.
Voice recognition has other applications in authentication and verification. Being able to identify someone and verify their access based on their voice can save a lot of time, though we are now getting to the point where voices may not be as secure as other biometric methods. Deep learning algorithms have made it possible to realistically mimic a voice using a computer using a technique called vocal synthesis. ‘Deep fake’ voices have been used in successful fraudulent activity that in one case cost an energy firm in the United Kingdom $250,000 in 2019.
As machine learning technology improves, vocal synthesis will become even more realistic over time. Unless technology improves to better recognize legitimate versus fake voices, voice recognition biometrics technology is better suited for non-security applications, particularly identification. This may be useful in consumer-based systems like smart homes, or enterprise solutions such as automatic transcriptions of meeting recordings that can attribute speakers by name.
Iris Scanning Technology
This form of biometrics technology is often seen in science fiction. It is similar to facial recognition in that it is contactless, but focuses only on one particular facial feature, namely the eye. One advantage to this is that there is less complexity to account for. Advanced facial recognition systems are not needed; instead, the system needs only recognize the features of the iris. You don’t necessarily have to be close to an eye to scan the iris, either. Tests at Carnegie Mellon University have demonstrated technology that can scan an iris at 40 feet away.
One advantage of this technology is that because it uses infrared sensors to analyze the iris, scanning the eye can even be done in low-light conditions.
Law enforcement's use of this technology for the identification of suspects is definitely one of the first things that may come to mind. However, this can also be a helpful authentication and verification method for both consumer and enterprise applications. Samsung’s Galaxy S9 and Note 9 smartphones both have iris scanning technology, demonstrating that this biometric method can be used on portable devices. This can be valuable not only to consumers but also for enterprise-level device security.
When compared against a single authorized user's biometric data, an iris scanner can authenticate a user nearly instantaneously. When identifying or verifying a user against a large database of hundreds of thousands of subjects, less than 20 seconds is sufficient time to authenticate.
Fingerprint Authentication Technology
Fingerprints have been in use for thousands of years for identification. They have particularly been useful in forensics technology, but recently they have also seen some use in consumer and enterprise security solutions. In 2003, the Fujitsu F505i pioneered the very first cell phone with a fingerprint sensor. It would later be popularized with Touch ID on Apple iPhones and various scanners on Android phones.
Fingerprint authentication technology works just like any other biometric method. By comparing the grooves and valleys of an individual’s finger against a pre-authorized image or a database of such images, they can be identified, verified, and/or authenticated. This can be done very quickly without disrupting the user experience.
However, one downside to fingerprint scanning is that it typically is not contactless. The user has to press their finger against the sensor in order for it to register. In some circumstances, this may not be desirable due to health concerns, especially with the global spread of the SARS-CoV-2 virus. However, it is possible to scan a fingerprint or entire hand via contactless methods. The LG G8 ThinQ smartphone uses a time of flight (ToF) sensor and infrared camera to detect the blood vessels in the hand of the user, all without requiring the user to press their hand against a surface.
Another downside to fingerprinting is that it can be inaccessible for groups of people with disabilities. Because of this limitation, it may be wise to invest in multiple forms of biometric authentication to maintain accessibility.
How AI Can Improve Biometric Authentication Systems
When it comes to security, improving the accuracy and efficiency of biometric authentication systems cannot always be done with human programming. Artificial intelligence and machine learning can help us make our systems more secure and efficient.
Biometric technologies can be split into two domains, physical and behavioral.
PHYSICAL BIOMETRIC TECHNOLOGY
Physical biometrics include everything that we have already discussed in this article. These are objective characteristics of a person like their face or fingerprints, DNA, and more. This must be converted into data that can be analyzed by the AI system and compared against a database for authentication purposes.
One of the cases where AI and ML prove most helpful is with facial recognition. Used extensively with augmented reality solutions, AI can help make facial recognition by computers much easier by analyzing facial features and matching them with a database.
BEHAVIORAL BIOMETRIC TECHNOLOGY
One of the most interesting trends that artificial intelligence makes possible is behavioral biometric technology. This uses the unique behavioral characteristics of how a subject interacts with the world, things that the user may not even realize about themselves. This is one of the most effective lines of defense against deep fake fraud attempts. Some of the more popular ways to measure behavioral biometrics are:
- Mouse activity
- Keystroke movement
- Touch screen press size, area, and pressure
- Mobile device motion
The Biometrics and Data Pattern Analytics Lab from the Autonomous University of Madrid developed BeCAPTCHA, a system for bot detection that uses behavioral biometrics. It’s entirely possible that behavioral biometrics can be used without the user’s knowledge, eliminating the need for annoying tests of the user’s humanity as CAPTCHA challenges have done for years. In the next few years, users may never again have to click on pictures of crosswalks and stoplights to prove they are ‘not a robot’ while browsing the Internet.
Importantly, behavioral biometrics can assist in ensuring security throughout an entire session. For example, if a user authenticates themselves and then leaves the room, unwittingly enabling an unauthorized user to gain access to their computer, this could pose a serious security risk. However, behavioral biometrics can detect the inconsistent behavior of the second user and restrict their access dynamically.
How Multimodal Biometric Authentication Solutions Work
Every form of biometrics technology has its unique set of pros and cons. None of them are universally effective. To improve the accuracy and effectiveness of biometric authentication technology, it’s important to layer security with multimodal biometric recognition solutions. We can see this in action in the following diagram:
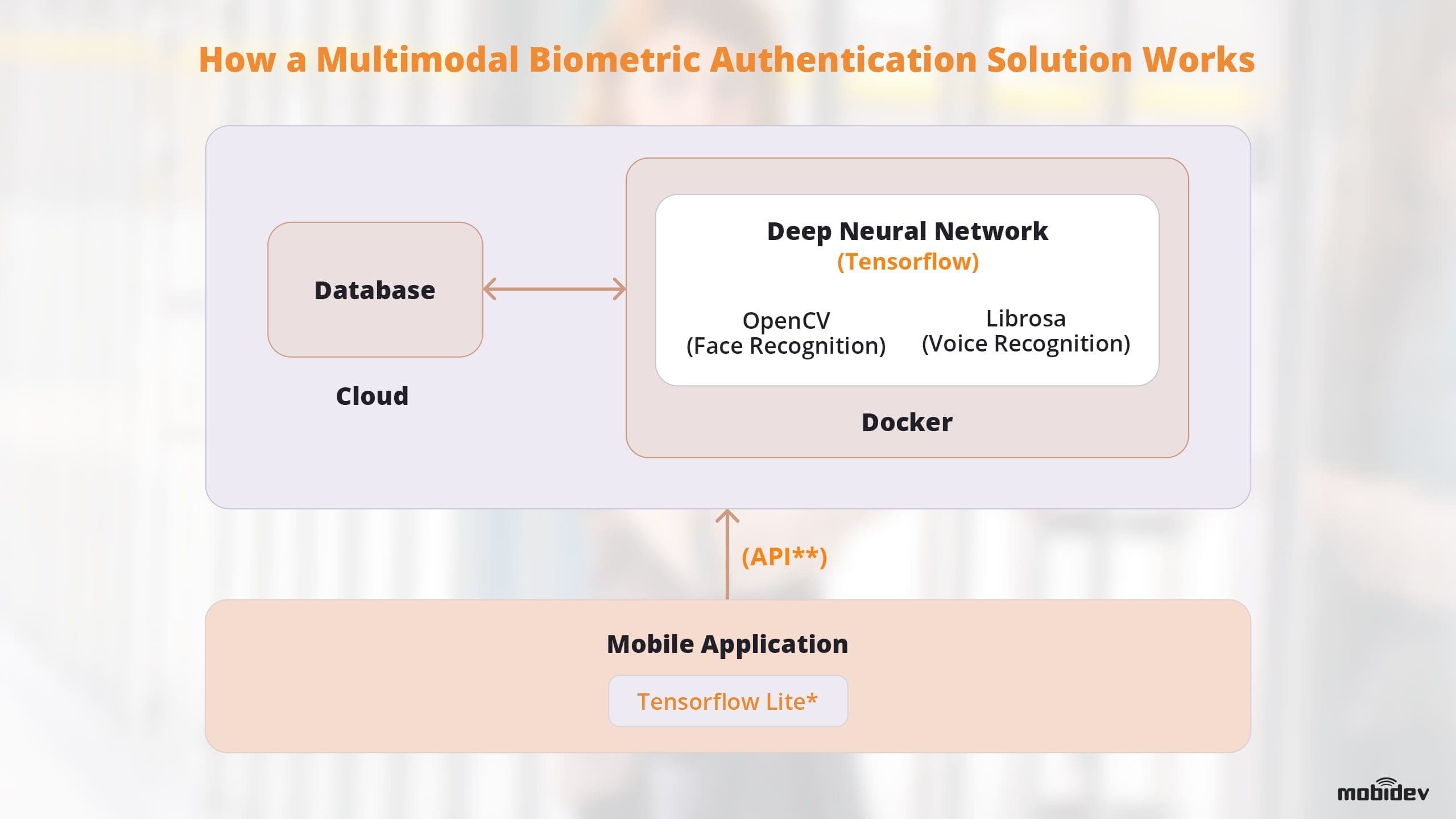
* Neural networks on mobile applications can be challenging to develop and implement. Neural networks can be integrated into applications using TensorFlow Lite, however, there are various limitations. Training your neural network models with the TensorFlow library can help. You will need to thoughtfully design the architecture of the application beforehand and put those requirements into consideration.
** If a native application is not possible, this process can be offloaded to the cloud to process the data like Rest API. However, this will incur additional networking resources and require an Internet connection.
Source: MobiDev
There is an Nvidia Docker that can simplify the deployment of the system, while a service provider (such as AWS) can provide an uninterrupted communication channel, computing power for neural networks, and a convenient interface for scaling your system.
TEST #1: FACIAL RECOGNITION
The user creates a photo-imprint that’s stored on the device using a camera. This biometric imprint is converted and normalized using the OpenCV library.
The face is identified using a photo, and all of the 64 landmarks detected by OpenCV are highlighted. A biometric verification landmark includes things like a distance from the bridge of the nose to the eye and other facial features.
These landmarks and a cutout image of the face are transferred to a deep neural network, which is trained using the TensorFlow library.
An eDNA feature vector is formed after neural network processing is completed. The feature vector collects the biometric characteristics of a particular person. The length of the vector is usually 2048 bits, but the actual vector length depends on the DNN architecture.
During verification, eDNA is issued and compared with the anchor record that was formed earlier. Reverse engineering is impossible because there is no access to the vector. The biometric system will periodically update this anchor record to match an individual’s changing appearance.
TEST #2: VOICE VERIFICATION
The user provides a voice sample through a microphone, which then gets processed by the Librosa library. The library reads the audio, transforms and converts it, and then transmits biometrics to the neural network (DNN).
An eDNA feature vector (2048 bits) is formed, which takes into account such biometrics as timbre, intonation, tempo, pitch, and other characteristics that the neural network was trained to respond to.
Case Study: AI-based Biometric Authentication Solution
By combining a microservice-based architecture, WebRTC, and machine learning-powered biometric recognition, we developed a single sign-on (SSO) biometric authentication solution for a US-based firm. Utilizing voice and facial recognition technology, we developed an enterprise verification-as-a-service (EVaaS) solution that uses the technologies and trends discussed earlier.
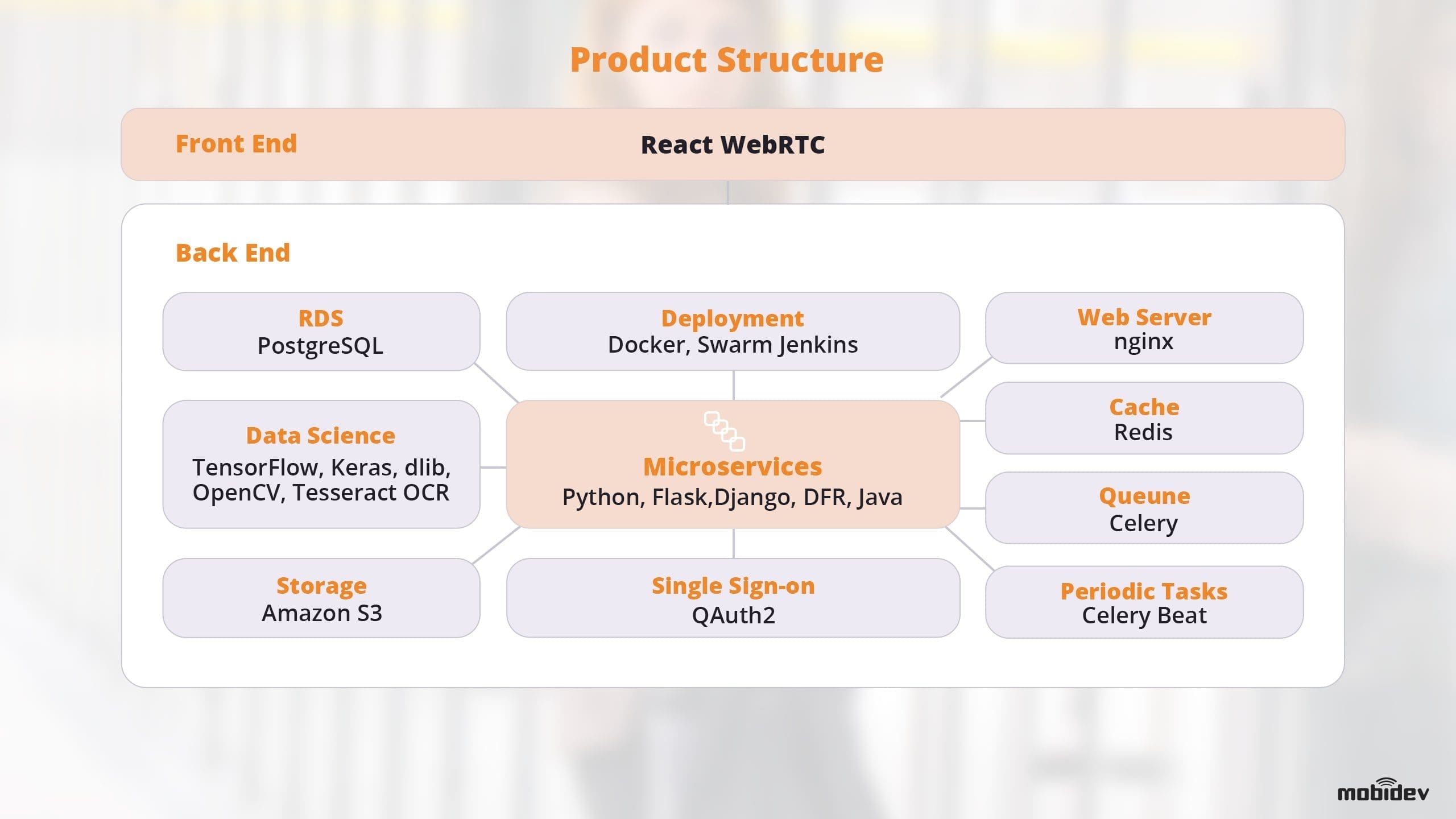
Source: MobiDev
This product proved that biometric authentication systems can be highly customizable and easy to use, powering a very simple user interface from behind the scenes. In addition, this example was able to integrate with existing systems via API.
Biometric Authentication Solutions Development
Securing systems is not a matter to take lightly. When sensitive information is on the line like protected health information or institutional data, it is extremely important to take the measures necessary to prevent data breaches. Failure to maintain a high level of security surrounding this information can result in fraud that can cost businesses tens or even hundreds of millions.
The Most Comprehensive IoT Newsletter for Enterprises
Showcasing the highest-quality content, resources, news, and insights from the world of the Internet of Things. Subscribe to remain informed and up-to-date.
New Podcast Episode

Navigating the Future of Embedded Computing
Related Articles





