Huge Vulnerability Discovered in the Ring Doorbell
Huge Vulnerability Discovered in the Ring Doorbell
- Last Updated: December 2, 2024
James Schaefer
- Last Updated: December 2, 2024



Last October, a botnet comprised of ~100,000 Internet of Things (IoT) devices, driven by a virus called Mirai, launched a DDOS attack against Dyn DNS. This attack disrupted service to several major websites including Amazon, PayPal, Twitter, Reddit, and Github.
This attack brought the Mirai Botnet into public light, and with it came very real questions about security in the IoT space. Mirai was able to grow so large so quickly by exploiting default admin passwords on common IoT devices, predominantly video cameras.
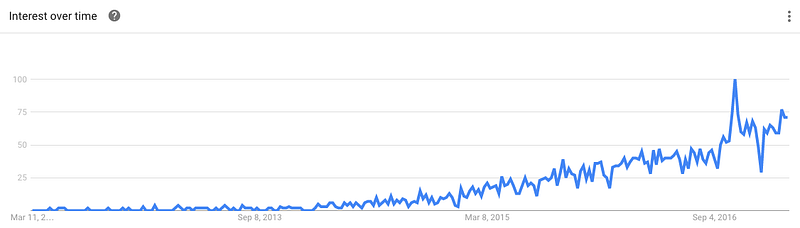
A quick look at Google Trends shows that around the time of the Dyn DNS attacks (Oct 21), interest in IoT security registered a huge spike. Since then, talk of IoT security has intensified, not just in how to prevent future botnets, but also in respect to how user data can be protected. However, talk about IoT security only does so much.
'As we’ve just seen with Ring, even if the customer-facing company cares deeply about security, if the firmware provider doesn’t then it doesn’t matter.'
Security Problems Continue to Persist in IoT
So what are we doing in response? In regard to the main component of the Mirai botnet, networked cameras, the concerning answer is that very little has been done. In fact, just this week, it was discovered that the Ring Doorbell, a popular connected camera and security product, is sending data to China.
Why? According to Ring, if the Ring device loses connectivity unexpectedly at the end of a transmission, it sends the final video/audio packets to an un-routable address, essentially throwing them away. Unfortunately for Ring, that isn’t what the device actually does, instead it routes packets to an IP address in China owned by Baidu, a Chinese search engine.
<!-- wp:paragraph --> <p>Besides raising serious privacy concerns about what exactly is being sent in the end-of-call packets and who may be receiving them, this behavior creates a potential back-door into the Ring device by opening a hole in the Wi-Fi network the Ring is on, such that data coming back from China can get through a router to to the device.</p> <!-- /wp:paragraph -->
<!-- wp:paragraph --> <p>In fact, because the device uses UDP, anyone willing to spoof the Chinese IP Address would be able to return traffic to a Ring Device if they could find it. This could, depending on the firmware of the Ring’s camera, leave it open to command-and-control protocols similar to what happened with the Mirai botnet.</p> <!-- /wp:paragraph -->
<!-- wp:heading --> <h2 id=" />Everyone Needs to Care About IoT Security
This kind of behavior probably isn’t isolated to just Ring, as most well-known IoT camera devices aren’t actually manufactured by the company selling them. In most cases these devices are actually manufactured overseas by companies like Dahua, Acti, and Hikvision.
This mean that the firmware on the camera often isn’t maintained by the manufacturer. So while consumers may be willing to trust Ring, by using the Ring Doorbell consumers are also unknowingly choosing to trust the manufacturer of the camera.
To further aggravate the problem, Ring might not be able to do anything to address this vulnerability. As mentioned, in all likelihood Ring doesn’t write the firmware on the camera.
In order for the Internet of Things to be secure, every stakeholder from the hardware manufacturer to the service creator has to take security seriously. As we’ve just seen with Ring, even if the customer-facing company cares deeply about security, if the firmware provider doesn’t then it doesn’t matter.
Until everyone takes IoT security seriously, instances like the Mirai Dyn DNS attacks will keep happening with the potential for much darker consequences. Delayed service to websites is one thing, but when the Internet of Things increasingly includes things like medical devices and transportation, the stakes become much higher.
Update: IoT For All spoke with a Ring representative January 31, 2019 who gave the following statement: "As a security company on a mission to reduce crime in neighborhoods, security is at Ring’s core and drives everything we do. This was not a security threat to Ring customers, however, we did change the protocol via a firmware update immediately. Ring dedicates significant time and money to product and network security. We have an in-house team that is constantly working to ensure Ring products are secure; we also work with several outside firms to do intrusion testing on all devices."
The Most Comprehensive IoT Newsletter for Enterprises
Showcasing the highest-quality content, resources, news, and insights from the world of the Internet of Things. Subscribe to remain informed and up-to-date.
New Podcast Episode

How Drones and Telecom Enable Aerial IoT
Related Articles


