IoT Security - Why we Need to Secure the Internet of Things
IoT Security - Why we Need to Secure the Internet of Things
- Last Updated: December 2, 2024
Calum McClelland
- Last Updated: December 2, 2024



IoT Security Needs to be Prioritized
To date, IoT security hasn’t been a priority. Instead of being viewed as an integral part of any IoT system, security has too often been an afterthought (or not thought of at all).
Going forward, security needs to be deeply considered in every aspect of an IoT system, whether that’s the physical device itself, the way it connects, cloud processing and storage, or the user-interface (you can read an explanation of how an IoT system actually works here).
If you’re a consumer, you need to make sure that any connected devices you purchase aren’t vulnerable and take the necessary steps to make sure those devices remain secure. If you’re a business, you need to make security a top priority for your products and maintain ongoing support to make sure any new vulnerabilities are quickly addressed.
But Why Does IoT Security Matter?
The Internet of Things will transform our world and create a tremendous amount of value. But as billions of new devices are connected to the internet and integrated into our daily lives, we open up new ways to cause harm.
“Dumb” devices that lack an internet connection are difficult to attack because you need physical proximity to the device. When it comes to “smart” devices, the very thing that makes them smart (i.e. connectedness) also opens up new avenues of attack from virtually anywhere.
Danger to Individuals
One of the dangers of these attacks is that there can be terrifying breaches of privacy. In 2013, hackers stole the personal information of 70 million individuals from Target, gaining access due to a connected HVAC system.
It’s also been shown that many baby monitors on the market can be easily hacked, allowing third-parties to watch the live video feeds or harvest video clips stored online. Beyond the extreme creepiness of someone watching your personal moments, hacking video cameras or even smart thermostats can tell a third-party whether you’re home, making it easier to burglarize.
In addition to breaches of privacy, digital attacks can also threaten personal safety. Security researchers Charlie Miller and Chris Valasek have demonstrated the ability to hack a Jeep Cherokee in motion, even shutting off the breaks and accelerator.
“Miller and Valasek’s full arsenal includes functions that at lower speeds fully kill the engine, abruptly engage the brakes, or disable them altogether. The most disturbing maneuver came when they cut the Jeep’s brakes, leaving me frantically pumping the pedal as the 2-ton SUV slid uncontrollably into a ditch. The researchers say they’re working on perfecting their steering control — for now they can only hijack the wheel when the Jeep is in reverse. Their hack enables surveillance too: They can track a targeted Jeep’s GPS coordinates, measure its speed, and even drop pins on a map to trace its route.”
It’s not just cars that can be hacked to physically harm people, a hacked elevator full of people or hacked devices that are life-critical in a hospital could also cause tremendous harm, perhaps being used as ransom.
These examples are alarming, and they should be, but it would be misguided to think that IoT security is only relevant to individuals. There are also huge threats posed by the current state of IoT security on a system-wide level, which is why IoT security is critical for everyone.
Dangers to Systems, Businesses, and Governments
As physical systems continue to be brought online and connected to the internet, physical damage can increasingly be caused by digital tools.
In 2009, US and Israeli designed and released a computer worm called Stuxnet to infect an Iranian nuclear enrichment facility. The code successfully infected industrial control systems causing centrifuges to malfunction and be destroyed.
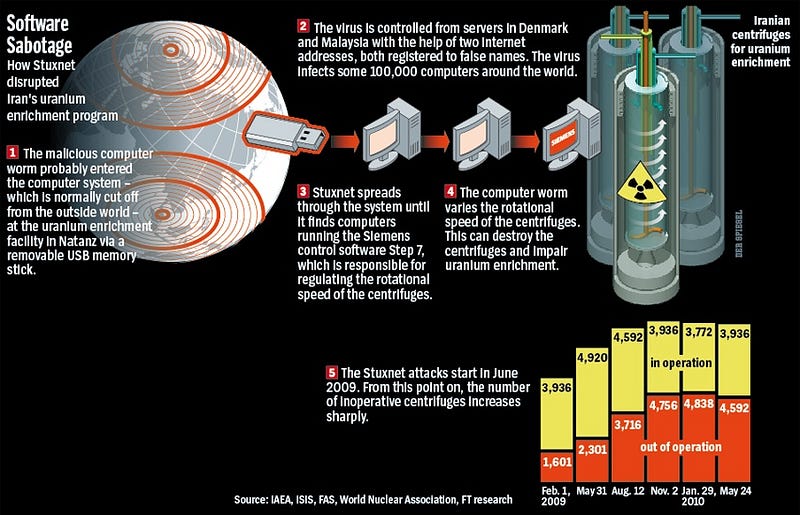
“If there is one lesson to be learned from well publicized cyber-attacks like StuxNet, it is that hacking is not just the domain of bored teenagers, hacking drones or even the small groups of motivated hackers. When the stakes are high enough, Cyber-attacks are multi-phased, multi-year efforts carried out by large, well-funded teams of hackers or even by nation states.” — The Internet of Secure Things, What is Really Needed to Secure the Internet of Things?
It may be tempting to consider these problems the responsibility of businesses and governments, but consumers play a critical role too. Why? Because IoT devices aren’t just targets for attack, they can be used as weapons themselves.
“the idea is that at the moment, IoT botnets are one of the biggest threats to internet stability, and there seems to be no stopping their growth because neither manufacturers nor consumers are concerned with IoT security, and as a result millions of new vulnerable devices are plugged into the internet every day, providing botlords with fresh new conscripts for their zombie armies.” — Ben Dickson, How the IoT industry will self-regulate its securit
A “botnet” refers to a group of computers that have been remotely accessed and compromised. The hackers then use those compromised computers (called bots or zombies) to forward transmissions to servers or other computers. When all of those bots forward to the same place and cause extremely high traffic, it’s known as a Distributed Denial of Service (DDoS) attack. By overwhelming servers with huge spikes in bandwidth, DDoS attacks take those servers down.
Back in October of 2016, the largest DDoS attack ever was launched on service provider Dyn using an IoT botnet. This lead to huge portions of the internet going down, including Twitter, the Guardian, Netflix, Reddit, and CNN.
This IoT botnet was made possible by malware called Mirai. Once infected with Mirai, computers continually search the internet for vulnerable IoT devices and then use known default usernames and passwords to login, infecting them with malware. These devices were things like digital cameras and DVR players.
Although this DDoS attack was simply inconvenient for many people, it’s not a stretch to imagine such an attack being directed in a more nefarious way, especially as more and more of the physical world relies on being online.
Securing the Internet of Things is critical, but why is IoT security such an issue? What are the barriers to addressing these issues? You can find out here in Part 2!
The Most Comprehensive IoT Newsletter for Enterprises
Showcasing the highest-quality content, resources, news, and insights from the world of the Internet of Things. Subscribe to remain informed and up-to-date.
New Podcast Episode

The State of Smart Buildings
Related Articles



