IoT Security in an Age of Insecurity
IoT Security in an Age of Insecurity
- Last Updated: December 2, 2024
Amanda Lopez
- Last Updated: December 2, 2024



Discussions about the Internet of Things (IoT) often focus on a “Security vs. Privacy” paradigm. However, last month author Susan Landau emphasized instead that discussions should focus on “Security vs. Security” at a New America event entitled Listening In: Cybersecurity in an Insecure Age.
[caption id="attachment_7281" align="alignnone" width="1632"]

In her same-titled book, Susan’s historical perspective, legislative knowledge, and cyberattack descriptions make a convincing case for the need to secure our data. She describes how security has matured slowly leading up to today’s strong-encryption found in corporate, government, and military environments.
A New Paradigm: "Security vs. Security"
Improving law enforcement is an example of “Security vs. Security.” Susan writes that investigators need to “learn the nitty-gritty details of how contemporary communications technologies work” to keep up with security-defeating techniques used by organized crime, nation-state attackers, and other bad actors.During her talk, Susan states that we haven’t really adapted to the digital revolution of the past 10 years. During the industrial revolution, securing access to a machine on the factory floor was much simpler, “With in-person authentication in factories, everybody knew everybody. But our mental models haven’t moved.”
“When you talk about building a front/back door into security, everybody has access to it eventually. When you make phones easy to open, it’s open to everybody to get at the software and the data. Instead, you have to educate everybody. Encryption is what will protect us.”
Don't Outlaw Encryption
Hardware security is what's new. Software security has been around a while now. Susan explains why the FBI’s arguments about making phones easy to open, is a bad idea. “You cannot outlaw encryption; it’s in applications. That battle is over.” Plus, “We all know about the DNC hack, [2016 Clinton campaign chairman, John] Podesta and others weren’t using 2-factor authentication.”“You cannot outlaw encryption; It’s in applications. that battle is over.”Most importantly for IoT, Susan argues that opening up security for FBI, DOJ and others “removes long-term the ability to use your phone as one of the factors in 2-factor authentication.”
Do Protect Civil Society
Besides 2-factor authentication, Susan sees ‘automatic security updates’ and ‘ephemeral communication’ (such as Snapchat’s disappearing messages) as a step in the right direction, especially to protect civil society. Automatic security updates fix a large piece of the problem. If it means I don’t get to do something and there are tradeoffs, I’m OK with that.”“Civil society is really threatened, for example an LGBT or a climate-change group. These organizations don’t have the funds to provide their own security and encryption. They need to rely on phone companies, and other tools to do it for them. There’s all kind of microdata that’s being collected. For example, Google and Apple collect the swipes on your phone to help design a better user experience. But they—or others—can use that microdata for negative reasons also.”
Susan doubts whether blockchain technology with 2-factor authentication will alleviate security challenges. “There are certain advantages to anonymous devices, but I don’t see it catching on for IoT devices. I don’t see it useful here with security encryption.”
[caption id="attachment_7074" align="aligncenter" width="970"]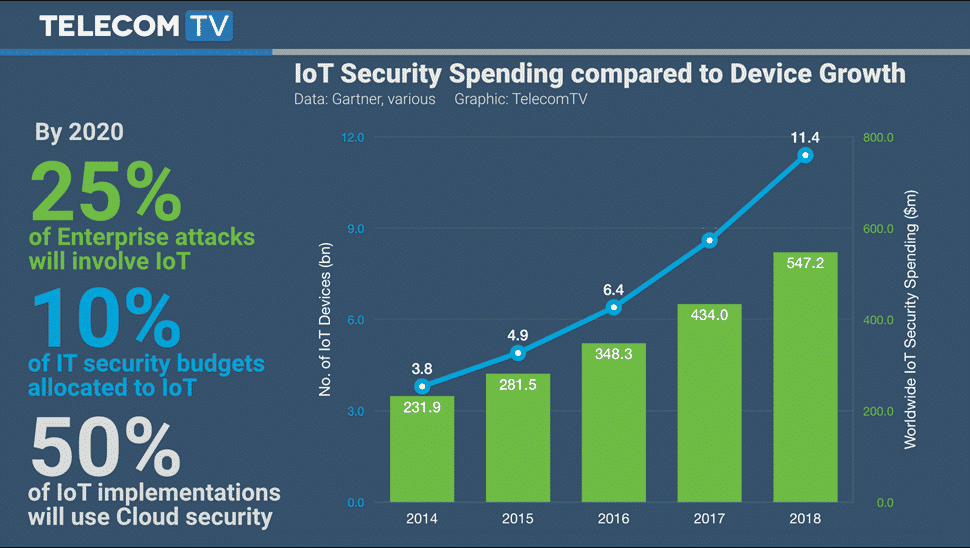
Don't Expect Users to Understand Security
To prevent current IoT security issues, such as hacking into an Amazon Echo, Susan suggests a regulation such as “If you cannot update the IoT device, then the device has a 2-year shelf life. It must die after two years.” In other words, device manufactures cannot expect consumers to understand security.In 2014, the President’s Council of Advisors for Science and Technology (PCAST) also concluded that, “Notice and choice don’t work. What you need to do is control use.”
Do Frame Laws to Promote Security
Susan’s idea of control is, “You need to frame the laws in a general way, not specific to a type of technology, which may change…We can talk about doing regulation. Any system that can’t be updated for security protection has only got a shelf-life of so much time, but so far we’ve been loath to regulate. So until we have regulation for security, [consumer protection is] not gonna happen. But that’s what I see as the solution.”Susan ends her talk with, “The most important arguments are about privacy. [Civil society] cannot protect themselves without encryption.” So essentially, security is a means to a secure end: protecting consumers' privacy.
The Most Comprehensive IoT Newsletter for Enterprises
Showcasing the highest-quality content, resources, news, and insights from the world of the Internet of Things. Subscribe to remain informed and up-to-date.
New Podcast Episode

Navigating the Future of Embedded Computing
Related Articles